Technology Vision for Cyber Security
‘Technology Vision for Cyber Security’ for Urban Co-operative Banks – 2020-2023
On 24th September, 2020, the RBI released Cyber Security Vision Framework for Urban Cooperative Banks (UCBs).
The Reserve Bank of India (RBI) has proposed to bring cyber security rules based on the size and complexity of urban cooperative banks (UCB) with an aim to bring the largest of them at par with other banks that run a full gamut of protections against online threats.
“The approach will ensure that the UCBs with high IT penetration and offering all payment services are brought at par with other banks having mature cyber security infrastructure and practices,” the central bank said in its technology vision document for 2020-23.
As per RBI – the UCBs with higher digital depth will now have to appoint Chief Information Security Officer (CISO), and set up various committees such as IT Strategy Committee, IT Steering Committee, etc. There has to be a board approved IT governance framework, and considering the implementation to be a costly process, “the responsibility for implementation, monitoring, compliance and response would have to be assigned from the Board level and percolate down till the end user,”
The Reserve Bank of India published the “’Technology Vision for Cyber Security’ for Urban Co-operative Banks (UCBs) – 2020-2023”. The Technology Vision Document aims at enhancing the cyber security posture of the Urban Co-operative banking sector against evolving IT and cyber threat environment.
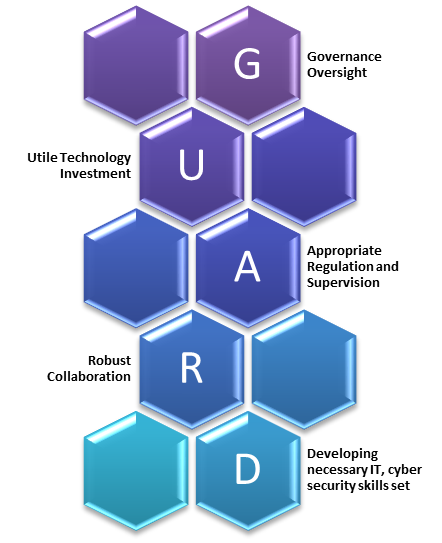
The Technology Vision Document for Cyber Security for UCBs has been formalized based on inputs from various stakeholders. It envisages to achieve its objective through a five-pillared strategic approach GUARD, viz., – Governance Oversight, Utile Technology Investment, Appropriate Regulation and Supervision, Robust Collaboration and Developing necessary IT, cyber security skills set.
With concerted efforts and involvement of all stake holders, the Technology Vision Document for Cyber Security for UCBs, with its 12 specific action points, aspires to
(a) Involve more Board Oversight over Cyber security;
(b) Enable UCBs to better manage and secure their IT Assets;
(c) Implement an offsite supervisory mechanism framework for UCBs on cyber security related controls;
(d) Develop a forum for UCBs so that they can share best practices and discuss practical issues and challenges; and
(e) Implement framework for providing awareness/ training for all UCBs.
The cyber security landscape will continue to evolve with wider adoption of digital banking channels, thus necessitating the UCBs to manage the associated risks effectively. Active collaboration within UCBs and their stakeholders would be necessary for sharing and coordinating various measures taken on cyber security aspects.
The implementation of the approach outlined in this Technology Vision document will strengthen the cyber resilience of the Urban Co-operative Banks.

HOW CAN WE HELP?
We bring to you team of highly trained, world recognized Cyber Professionals with a combined experience of more than 15 Years, and core BFSI IT & IS project management expertise in various small and large setups. Where we qualified successfully and were awarded projects with scope including capacity planning, surveillance audits, datacenter design and ISO 27001 implementation.
For UCB, we understand the ‘Vision for Cyber Security’ for UCBs – 2023
And we can help you in the journey of enhancing the cyber security posture of your institution (bank) against evolving IT and cyber threat environment through the RBI five-pillared strategic approach GUARD:
Governance Oversight,
Utile Technology Investment,
Appropriate Regulation and Supervision,
Robust Collaboration and
Developing necessary IT, cyber security skills set.
WHAT DO WE HAVE TO OFFER?
We can be your one stop shop, for all your IT, IS and Cybersecurity requirements, and thereby establishing a long-term relationship – such that we serve you as your strategic advisor on matters related to Cybersecurity. The five pillar and 12 controls as listed below will be the guiding objectives for your bank’s CS/IS/IT program.
Governance Oversight
i. Focus on Board Oversight over Cyber security
ii. IT Vision document
Utile Technology Investment
iii. Creation of reserve/ fund for implementation of IT/ cyber security projects
iv. Management of Business IT Assets
v. Banking Services Availability
Appropriate Regulation and Supervision
vi. Supervisory reporting framework
vii. Appropriate guidance in implementing secure practices
Robust Collaboration
viii. Forum to share best Practices and discuss practical issues and challenges
ix. CISO Forum for UCBs
x. Adoption of Cloud Services – Phase I
Developing necessary IT, cyber security skills set
xi. Imparting technical Skills to manage IT and Cyber Security
xii. Providing awareness/ training for all UCBs on cyber security
NEED OF DEDICATED CYBERSECURITY PARTNER
As cyber threats to the banking industry evolve, the information security risk to financial institutions matures.
Financial services organizations recognize the changing security landscape and cite avoiding data breaches as their primary mandate, with banking compliance becoming their second most important driver.
Extremely sensitive and valuable data resides in the financial services sector—everything from personally identifiable information (PII) to check routing data to global stock and investment algorithms. The loss of this data and intellectual property has a major effect on a bank’s brand reputation and customer loyalty. When consumers and business customers place their trust and their money in your institution, your reputation for information security is paramount.
While in comparison to several other sectors, banks (ALL KINDS) are definitely seen to be more proactive in investing and improving security practice, such measures may still be inadequate considering the challenges with the traditional approach to IT security are:
· Proliferation of attack vectors and enhanced attack surface
· Proliferation of digital and shifting customer preference
· Sophistication of threat actors and enhanced targeting of banks
· Banking increasingly operating as a ‘boundary-less’ ecosystem
OUR CUSTOMIZED UCB IS & CYBER SECURITY SOLUTIONS
With our strong & exclusive BFSI specific know-how, you will receive tailor-made cyber security services meeting your institution needs, such as:
· Information Security ( IS ) Guidelines
· Basic Cyber Security and Resilience Requirements.
· Baseline Cyber Security and Resilience Requirements – Level I
· Vendor/Outsourcing Risk Management
· Baseline Cyber Security and Resilience Requirements (in addition to the requirements given in Annex I) – Level II
Network Management and Security
Secure Configuration
Application Security Life Cycle (ASLC)
Change Management
Periodic Testing
User Access Control / Management
Authentication Framework for Customers
Anti-Phishing
Data Leak Prevention Strategy
Audit Logs & Incident Response and Management
· Baseline Cyber Security and Resilience Requirements (in addition to the requirements given in Annex I & II) – Level III
Network Management and Security
Advanced Real-time Threat Defence and Management
Maintenance, Monitoring, and Analysis of Audit Logs
User / Employee/ Management Awareness
Risk based transaction monitoring
· Baseline Cyber Security and Resilience Requirements (in addition to the requirements given in Annex I, II & III) – Level IV
Arrangement for continuous surveillance – Setting up of Cyber Security Operation Centre (C-SOC)
Participation in Cyber Drills
Forensics and Metrics
IT Strategy and Policy
IT and IS Governance Framework
Chief Information Security Officer (CISO)
OUR OTHER STANDARD BFSI OFFERINGS:
ü IS ( Information System ) Audit
ü Assessment of Cyber Security controls (Baseline, Level I, II, III AND IV)
ü Remediation of previous audit findings (Compliance).
ü Review and preparation of IS and Cybersecurity Policies.
ü Vulnerability Assessment and Penetration Testing (VAPT)
ü SOC as a Service.
ü Business Continuity
ü Cyber Attack Drills
ü Embedded System Security Audit
ü Cyber Intelligence
ü Code Review & Audit
ü Security Training & Staff Skill Building
ü Customer Education
ü Data Protection & Privacy Assessments
ü Virtual CISO and DPO
ISO Certification and surveillance audits

